
Attack by the APT group Charming Kitten
Investigate the attack based on the activities of a real APT group Study the most up-to-date techniques and tactics of threat actors to be prepared for real-life cyberattacks
New version
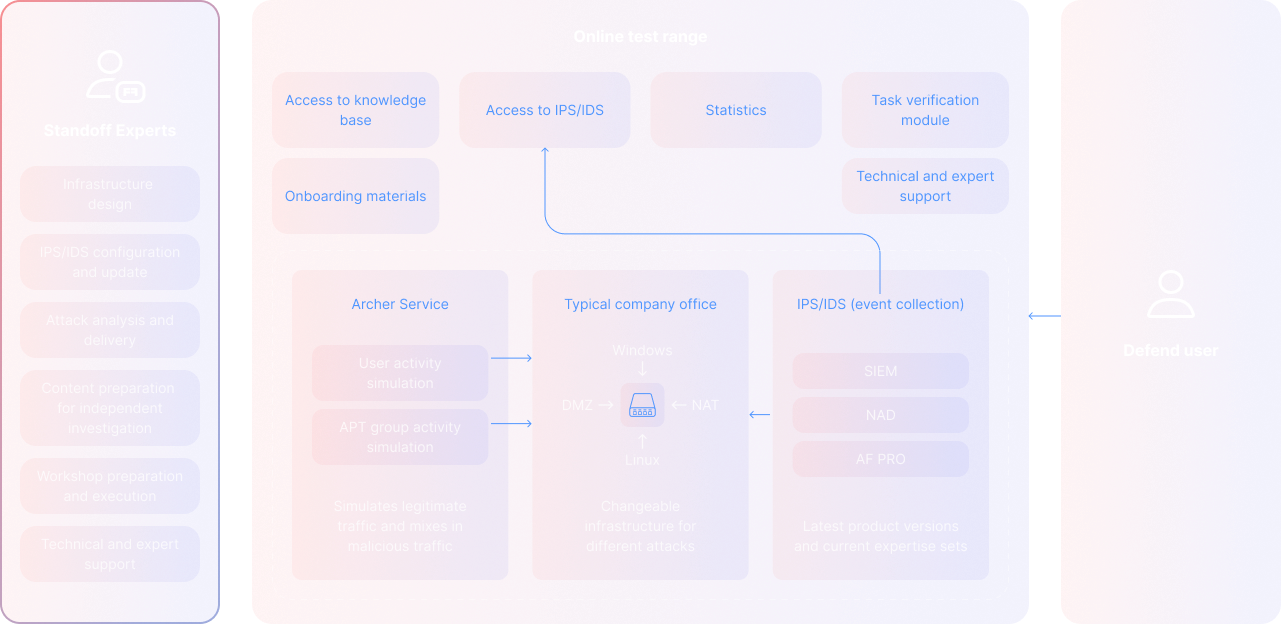
The cyberrange where infosec teams can master their APT attack detection and investigation skills online 24/7
With the Standoff Defend cyberrange, you can enjoy a unique experience in a safe environment, realistic infrastructure, and round-the-clock access.
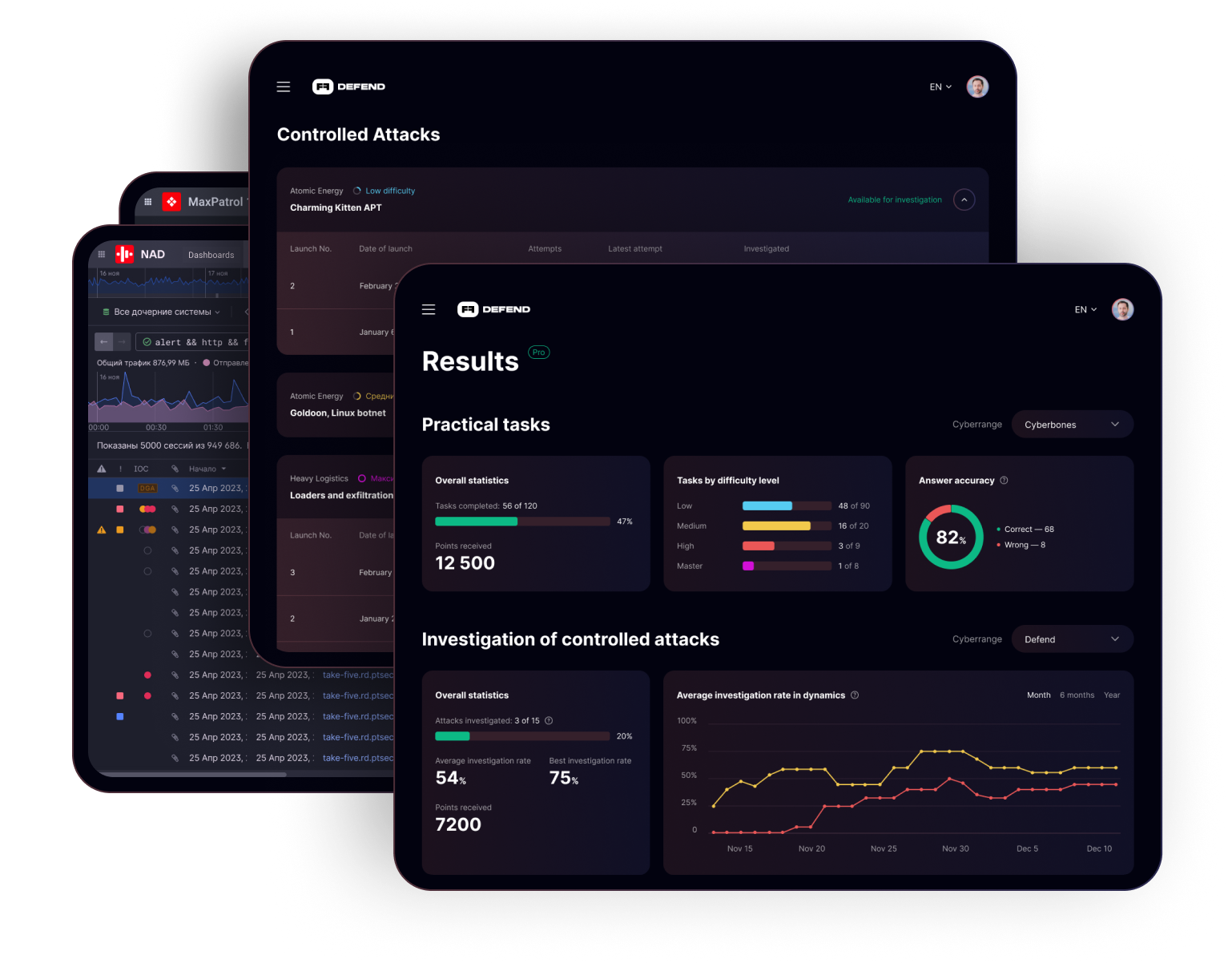
Individual and team analytics with comprehensive reports provide objective metrics to assess performance dynamics.

Train within an interconnected infrastructure of 1,500+ VMs and 500+ software units, closely resembling the ones you deal with in your everyday work.

We accurately simulate tactics used by APT groups so that you can engage with authentic attack scenarios.

Investigate the attack based on the activities of a real APT group Study the most up-to-date techniques and tactics of threat actors to be prepared for real-life cyberattacks

For businesses and cybersecurity professionals
| Standoff Cyberbones online simulator | Standoff Defend cyberrange | Standoff Cyberbattle | |
|---|---|---|---|
| Objective | ObjectiveSelf-guided practice in incident investigation using information security tools | ObjectiveComprehensive development of defensive security skills with mentor support | ObjectiveIntensive assessment of the team's readiness for real-time cyberattack response |
| Features | Features
| Features
| Features
|
| Task types | Task types Tasks based on Standoff Cyberbattle incidents | Task types
| Task types
|
| Attack format | Attack format Incidents from past Standoff cyberbattles | Attack format
| Attack format Live hacker attacks |
| Training format | Training formatSelf-guided | Training formatIndividual and team-based with mentor support | Training formatTeam-based with optional mentor support |
| Duration | Duration3 or 12 months | Duration12 months | Duration3–5 days |
| Mentor support | Mentor supportExpert support via Telegram bot | Mentor supportIndividual and team mentoring | Mentor supportOptional |
| Number of security tools | Number of security tools5 | Number of security tools5 | Number of security tools5 or more |
| Number of team members | Number of team membersFrom 5 to 15 | Number of team membersUp to 15 | Number of team membersUp to 15 |
| Service manager | Service manager— | Service manager | Service manager |
| Supplementary materials | Supplementary materials Quick start guides for security tools | Supplementary materials
| Supplementary materialsOptional |